Eduphoria supports Secure Assertion Markup Language (SAML), which lets you provide single sign-on (SSO) access to Eduphoria staff and student accounts. With SSO, users can sign in once using their organization’s sign-in credentials to gain access to multiple systems and service providers, including Eduphoria products.
Caution: To support electronic signatures with SAML, we require users to authenticate with the IdP every time they access the software. This ensures that the proper user is logged in if a different user signed a document on the machine earlier.
The following instructions apply to configuring Active Directory Federation Services (AD FS) in Windows Server 2016 and 2019 for SAML 2.0. Some information and screens may look different in older versions.
Warning: Activating SAML authentication will prevent users from being able to login with an Eduphoria account. If you activate SAML with errors in the configuration setup, you will need to contact the Eduphoria support team to disable SAML due to the fact that you won't be able to log in. Eduphoria's support team must be made aware of when your district is making the configuration change so they can be on standby.
Requirements for AD FS and SAML 2.0
Before you begin the process to configure AD FS for SAML, ensure to meet the following requirements first:
The organization either has a SAML server with provisioned users or is connected to an identity repository such as Microsoft Active Directory or LDAP. Options include using an in-house SAML server such as RapidIdentity or AD FS, Okta, OneLogin, or Ping Identity.
If you are using an AD FS server, you must enable forms-based authentication. Eduphoria does not support Windows Integrated Authentication (WIA).
Eduphoria-bound traffic is over HTTPS, not HTTP.
Requirements for Supporting Student SSO With SAML
AD FS and SAML can be configured to authenticate students as well as staff members. To authenticate students, you must meet the following requirements:
Students must log in with a username that matches their student ID from the Student Information System (SIS), or that ID must be present in some AD field.
Students must be in a single Student Group or be nested in a Student Group within the top-level Student Group. For instance, a top-level Student Group named All Students may have sub-groups within it like High School Students, Elementary Students, etc.
If the above requirements are met, you can create one additional Claim Rule to specify an authenticated account is a student once you reach that step.
Configuring SAML in Eduphoria
Step 1: Log in to Eduphoria and select Management.
.png)
Step 2: From the main menu, select the Security Settings gear icon.

Step 3: From the resulting drop-down menu, choose Directory Services and Student Sign-On.
.png)
Step 4: Go to the SAML tab.
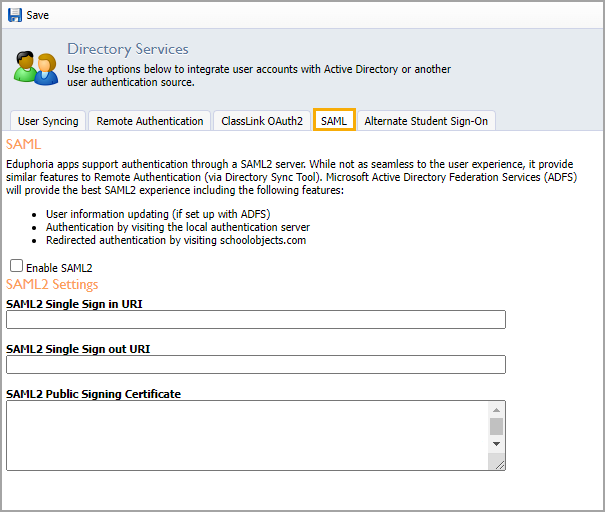
Step 5: Below are examples of what the SAML2 Single Sign-In URI and SAML2 Single Sign-Out URI should look like. Change the beginning of these URLs to match your AD FS or AD FS WAP URLs:
SAML2 Single Sign-In URI:
https://yourservicename.yourdomainname.com/adfs/lsSAML2 Single Sign-Out URI:
https://yourservicename.yourdomainname.com/adfs/lsTo acquire the SAML2 Public Signing Certificate, first download the metadata file from your AD FS server. Modify the link below and replace "yourservicename.yourdomainname.com" with the URL of your AD FS or AD FS WAP server and put it in a browser:
https://yourservicename.yourdomainname.com/FederationMetadata/2007-06/FederationMetadata.xmlA Fedaration Metadata XML file should download. Open the file and copy the entire value within the first tags. Paste the value in the SAML2 Public Signing Certificate box.
Warning: Do not check the box to Enable SAML2 yet. This will be included in the final phase of steps.
Step 6: Click Save.
Configuring AD FS
Step 1: In AD FS Management, open Relying Party Trusts.
Step 2: Choose the Add Relying Party Trust… action.
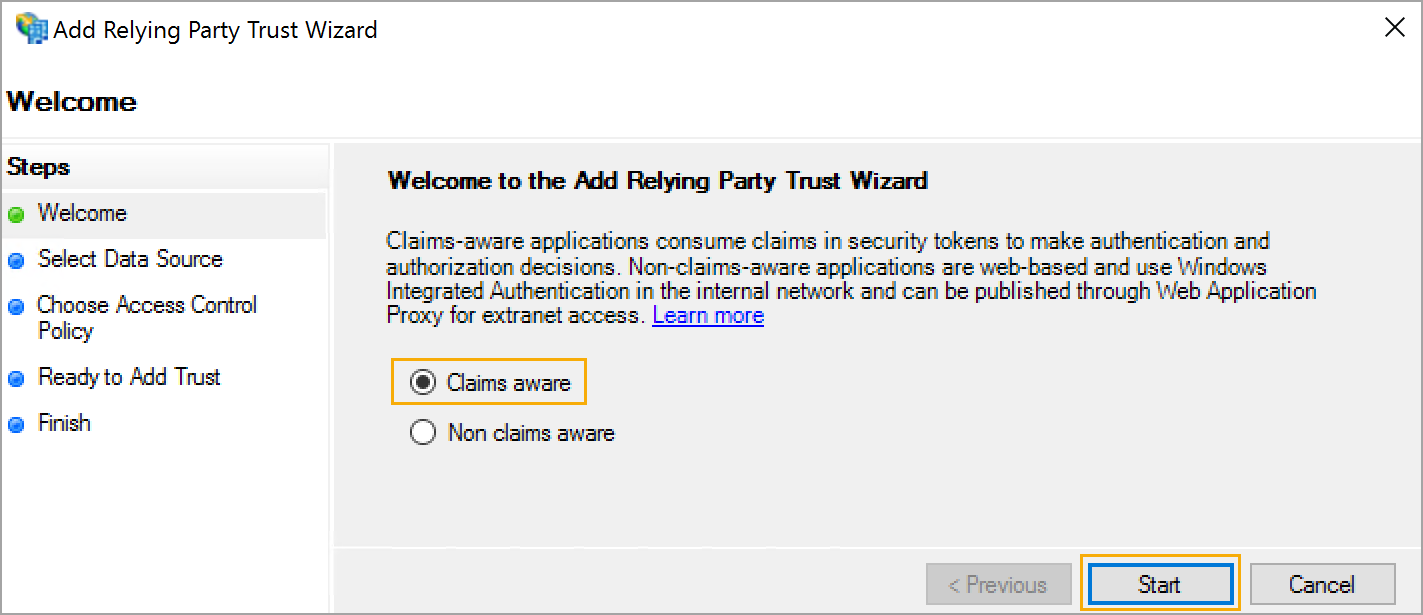
Step 3: On the first screen of the wizard, choose Claims aware, then click Start.
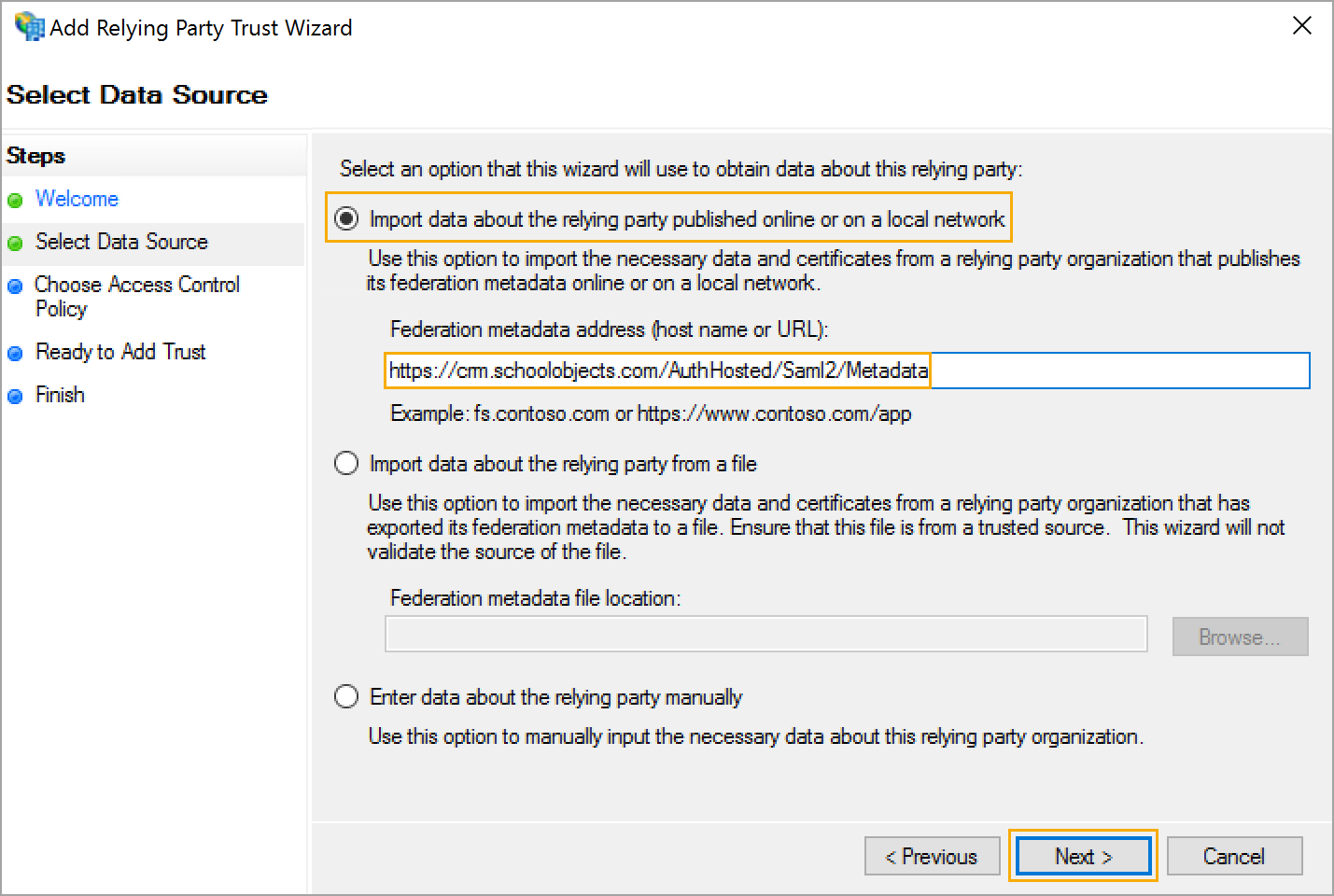
Step 4: Choose Import data about the relying party online or on a local network.
Enter the following URL:
https://{districtUrl}.schoolobjects.com/AuthHosted/Saml2/Metadata Click Next.
Step 5: For the display name, enter Eduphoria and click Next.
Step 6: On the next screen, limit permissions to only those who should have access to Eduphoria Apps. This should include most or all staff.
Click Next through the remaining screens and exit the configuration.
Configuring Claim Rules
Step 1: Once complete, right-click on the new Eduphoria Relying party and choose the Edit Claim Issuance Policy… action.
On the screen that pops up, choose Add Rule. A new wizard will start.
Step 2: Choose Send Claims Using a Custom Rule from the drop-down menu, then click Next.
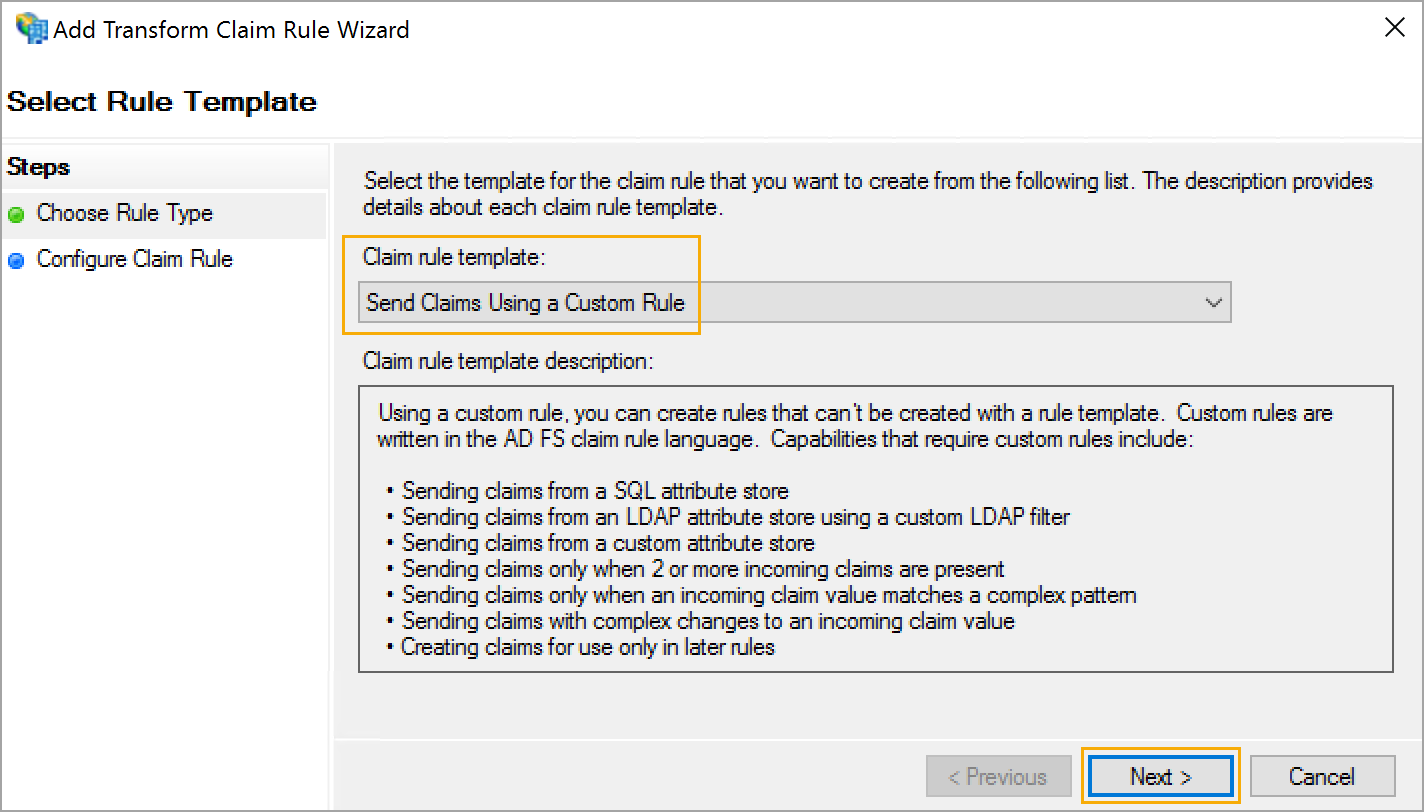
Step 3: Give the claim rule a name, such as AD Claims.
Enter the text below for the Custom Rule:
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> issue(store = "Active Directory",
types = ("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/privatepersonalidentifier",
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"),
query = ";givenName,sn,mail,objectGUID,sAMAccountName;{0}", param = c.Value);Your screen should look like the example below.
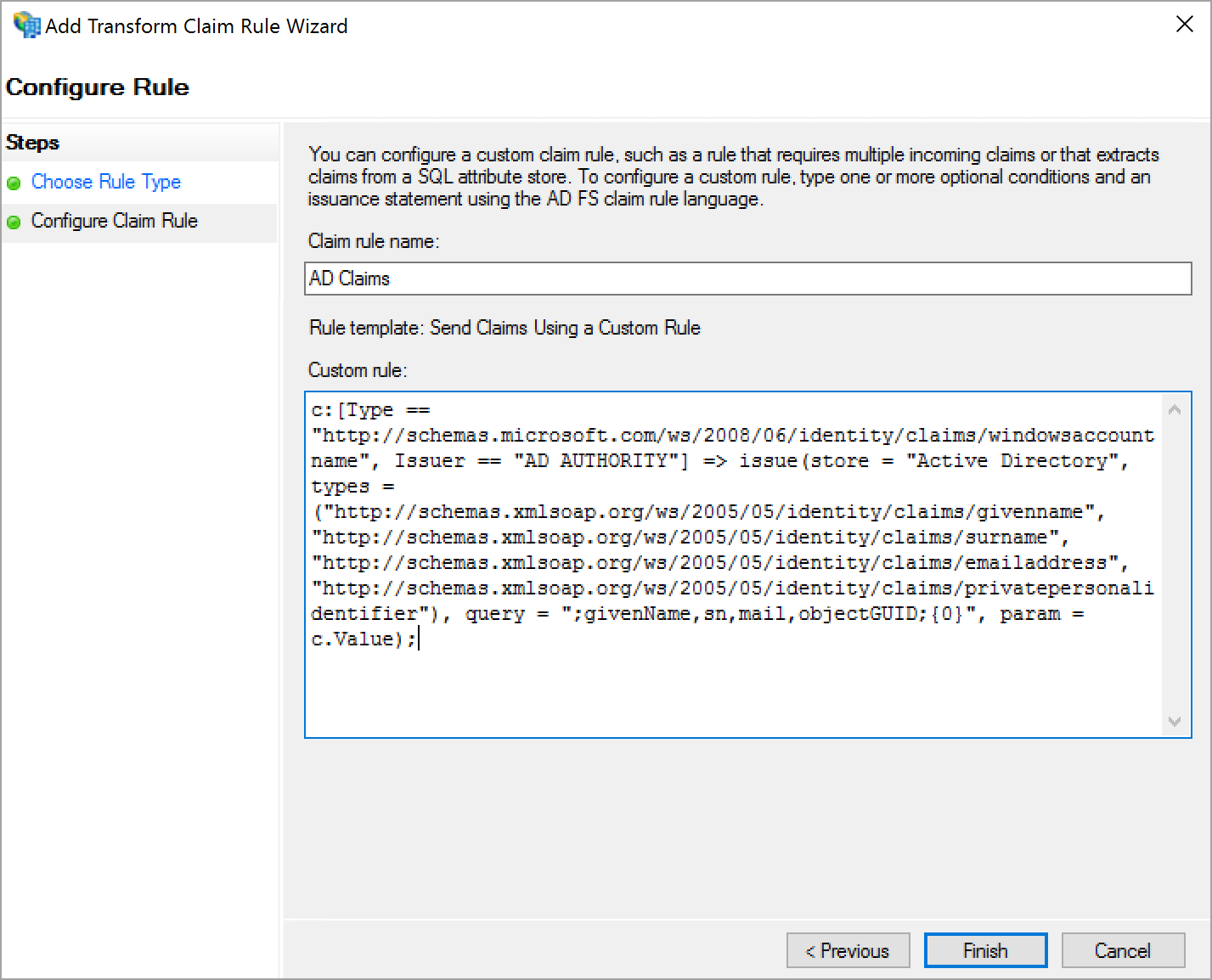
Step 4: Select Finish, then click OK on the Claims Issuance Policy window.
Step 5: At the Claim Issuance Policy screen, click Add Rule again. A new wizard will start.
Step 6: On the first screen, choose Send Claims Using a Custom Rule from the drop-down menu, and click Next.

Step 7: Give the claim rule a name, such as Name ID.
Enter the text below for the Custom Rule:
c:[Type == "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"]
=> issue(Type = "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier",
Issuer = c.Issuer, OriginalIssuer = c.OriginalIssuer,
Value = c.Value, ValueType = c.ValueType,
Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/format"] = "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress");Step 8: Select Finish, then click OK on the Claims Issuance Policy window.
Creating a Claim Rule for Student Accounts
If you have met the requirements to authenticate students through AD FS and SAML, you can configure a Claim Rule to specify an authenticated account is a student.
Step 1: At the Claim Issuance Policy screen, click Add Rule. A new wizard will start.
Step 2: Choose Send Group Membership as a Claim from the drop-down menu, and click Next.
Step 3: Give the claim rule a name, such as Student Group.
Step 4: Select a User’s group that would apply to all students.
Step 5: Choose Role for the Outgoing claim type. For the Outgoing claim value, enter student.
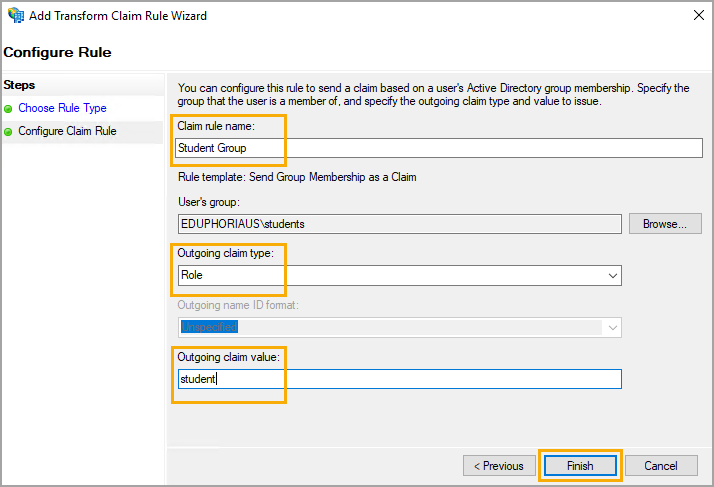
Step 6: Select Finish, then click OK on the Claims Issuance Policy window.
Enabling SAML
Step 1: Log in to Eduphoria and select Management.
.png)
Step 2: From the main menu, select the Security Settings gear icon.

Step 3: From the resulting drop-down menu, choose Directory Services and Student Sign-On.
.png)
Step 4: Go to the SAML tab.
Step 5: Select the Enable SAML2 checkbox.
Step 6: Click Save. Your AD FS configuration for Eduphoria is complete.